Cloudflare
Inhaltsverzeichnis
Cloudflare
SSH via Argo
Manual Video
https://www.youtube.com/watch?v=lq7WpGJZvk4
https://developers.cloudflare.com/cloudflare-one/tutorials/ssh
Named Tunnel new
Migration to Named Tunnel (Neue Version ab 01.12.22)
newest installation:
go to
https://one.dash.cloudflare.com/ Networks Tunnels
old:
- Install newest Cloudflare if not newest:
wget -q https://github.com/cloudflare/cloudflared/releases/latest/download/cloudflared-linux-amd64.deb && dpkg -i cloudflared-linux-amd64.deb
- Stop the old cloudflared Tunnel
sudo systemctl stop cloudflared
- Create a Tunnel:
cloudflared tunnel create <TUNNEL-NAME>
zB:
cloudflared tunnel create wega11
- Route traffic to your tunnel to create routes that your tunnel will serve.
cloudflared tunnel route dns <TUNNEL-NAME> tunnel.example.com
zB:
cloudflared tunnel route dns wega11 tunnel.ypsomed.online
- If it gives an error like this:
root@wega11:~# cloudflared tunnel route dns wega11 access.domain.com Failed to add route: code: 1003, reason: An A, AAAA, or CNAME record with that host already exists. root@wega11:~#
.. do this:
Delete the AAAA DNS Record on https://dash.cloudflare.com -> DNS -> Records completly
...and redo the step before
- Change /etc/cloudflared/config.yml file to this:
url: http://localhost:8000 tunnel: <Tunnel-UUID> credentials-file: /root/.cloudflared/<Tunnel-UUID>.json
oder (evt alt):
tunnel: d04fd56b-e28f-49a3-b055-f31d9eee9a17
credentials-file: /etc/cloudflared/d04fd56b-e28f-49a3-b055-f31d9eee9a17.json
ingress:
- hostname: access.domain.com
service: https://access.corp.itsroot.biz:443
- hostname: access2.domain.com
service: https://access2.corp.itsroot.biz:8443
# - logfile: /var/log/cloudflared_ecar.log
# Note that the last rule is the catch-all rule and is required.
- service: http_status:404
- Change /etc/systemd/system/cloudflared.service file to this:
[Unit]
Description=cloudflared
After=network.target
[Service]
TimeoutStartSec=0
Type=notify
ExecStart=/usr/local/bin/cloudflared --autoupdate-freq 24h --config /etc/cloudflared/config.yml tunnel run
Restart=on-failure
RestartSec=5s
[Install]
WantedBy=multi-user.target
- Start the Service. Thats it
Argo Tunnel old
Short
https://developers.cloudflare.com/cloudflare-one/connections/connect-apps/configuration/config
Without specifying --config, cloudflared will default to reading ~/.cloudflared/config.yml. An example config.yml for the above command could look like:
hostname: test.example.com url: http://localhost:8096 logfile: /var/log/cloudflared.log hello-world: false
Linux
run as Service
https://developers.cloudflare.com/argo-tunnel/reference/config/
https://developers.cloudflare.com/argo-tunnel/reference/service/
sudo cloudflared service install
If you have already logged in and have a configuration file in ~/.cloudflared/, these will be copied to /etc/cloudflared/.
If you do not have a configuration file, you will need to create a config.yml file with fields listed above. You can pass a custom file by running cloudflared --config CONFIG-FILE service install.
evt noch
sudo cloudflared enable install
Config file
/etc/cloudflared/config.yml
hostname: sub.domain.ch url: http://localhost:80 logfile: /var/log/cloudflared.log
Service File auf autoupdate umbiegen
/etc/systemd/system/cloudflared.service
[Unit] Description=Argo Tunnel (%I) After=network.target [Service] TimeoutStartSec=0 Type=notify ExecStart=/usr/local/bin/cloudflared --config /etc/cloudflared/config.yml --origincert /etc/cloudflared/cert.pem --autoupdate-freq 24h Restart=on-failure RestartSec=5s [Install] WantedBy=multi-user.target
dann noch
sudo systemctl daemon-reload
und
sudo systemctl restart cloudflared
Windoof
Install cloudflared
Once cloudflared is installed:
Navigate to the Downloads folder. Right-click on the ZIP folder and select Extract All to extract the executable. Next, open PowerShell. Navigate to the same Downloads folder. Run the cloudflared.exe executable as an administrator to confirm the installation, replacing the path in the example below with the specifics of your directory:
PS C:\Users\Administrator\Downloads\cloudflared-stable-windows-amd64> .\cloudflared.exe --version
https://developers.cloudflare.com/cloudflare-one/connections/connect-apps/install-and-setup/setup
Updating cloudflared
You can update cloudflared by running the following command.
cloudflared update
The update will cause cloudflared to restart which would impact traffic currently being served. You can perform zero-downtime upgrades by using Cloudflare's Load Balancer product or by using multiple cloudflared instances.
Authenticate cloudflared
Follow these steps to authenticate cloudflared:
1. Log in to your Cloudflare account with the following command:
cloudflared tunnel login
2. The command will attempt to open a browser window and prompt you to authenticate with your Cloudflare account.
If running on a headless system, copy the link and paste it into a browser.
3. Once authenticated, Cloudflare will return a certificate file, cert.pem, that will give this instance of cloudflared the ability to:
- Create and delete Tunnels
- Modify DNS records in your account
The file is required if you want to:
- Create new Tunnels
- Change DNS routing from cloudflared
The file is not required if you want to:
- Run an existing Tunnel
- Manage routing from the Cloudflare dashboard
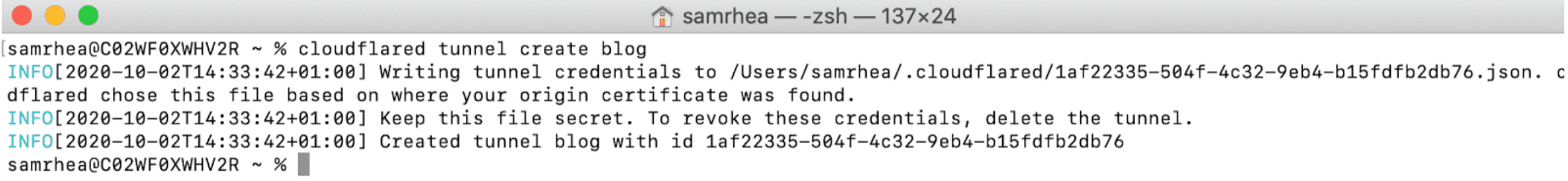
Create a tunnel
NOTE: Tunnels created in this method do not currently display in the Traffic tab of the Cloudflare dashboard. These connections will be added to the dashboard in a future release.
To create a Tunnel, run the following command:
cloudflared tunnel create <NAME>
Replace <NAME> with the name you want to give to the Tunnel. The name assigned can be any string and does not need to relate to the hostname where traffic will be served.
This command will create a Tunnel with the name provided and associate it with a UUID. The relationship between the UUID and the name is persistent. The command will not create a connection at this point.
Creating a Tunnel generates a credentials file for that specific Tunnel. This file is distinct from the cert.pem file. To run the Tunnel without managing DNS from cloudflared, you only need the credentials file.
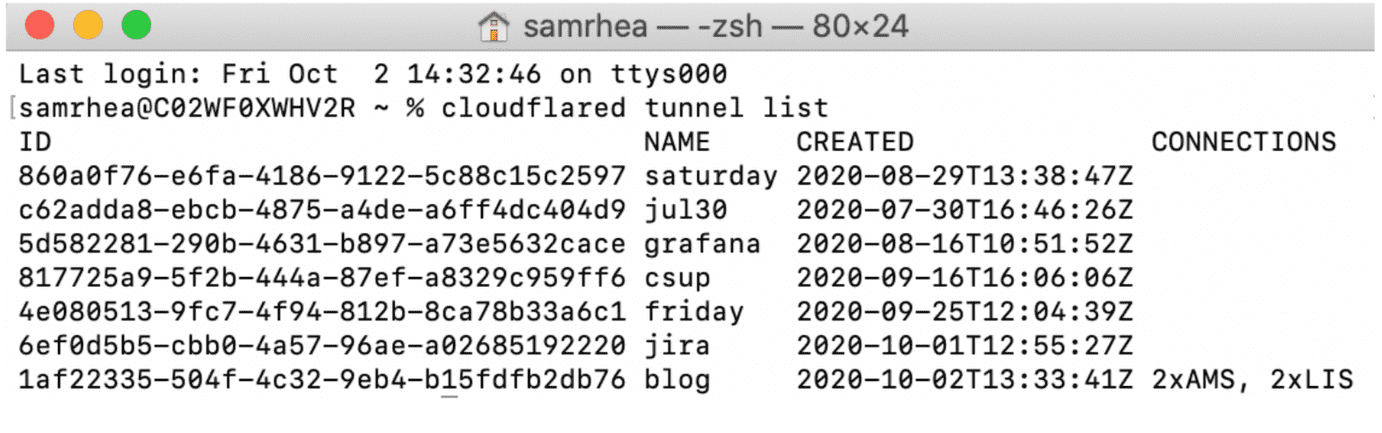
List available Tunnels
cloudflared can list all created Tunnels in your account, as well as those actively connected to Cloudflare, by running the following command:
cloudflared tunnel list
Note: the command requires the cert.pem file.
Revoke and delete a Tunnel
Revoke and delete a Tunnel
You can delete an existing Tunnel with cloudflared. To delete a Tunnel, run the following command:
cloudflared tunnel delete <NAME>
NOTE: The command requires the cert.pem file.
If there are still active connections on that Tunnel, then you will have to force the deletion with:
cloudflared tunnel delete -f <NAME>
This will cause those connections to be dropped.
Deleting the Tunnel also invalidates the credentials file associated with that Tunnel, meaning those connections can not be re-established.
Arguments
Tunnel commands
All tunnel-related commands are prefixed with tunnel. For example:
cloudflared tunnel --origincert ~/cert.pem --config ~/tunnel.yaml run mytunnel
Tunnel-related commands include creating, deleting and running tunnels with
cloudflared tunnel create <TUNNELNAME> cloudflared tunnel delete <TUNNELNAME> cloudflared tunnel run <TUNNELNAME>
You can also list all tunnels with
cloudflared tunnel list
Tunnel commands --config --autoupdate-freq --no-autoupdate --origincert --no-tls-verify --metrics --metrics-update-freq --tag --loglevel --proto-loglevel --retries --pidfile --logfile --help --version
--config
Syntax Default
--config value ~/.cloudflared/config.yml
Specifies a config file in YAML format.
--autoupdate-freq
Syntax Default
--autoupdate-freq 24h
Autoupdate frequency. See also --no-autoupdate.
--no-autoupdate
Syntax Default
--no-autoupdate false
Disables periodic check for updates, restarting the server with the new version. See also --autoupdate-freq. Restarts are performed by spawning a new process that connects to the Cloudflare edge. On successful connection, the old process will gracefully shut down after handling all outstanding requests.
--origincert
Syntax Default Environment Variable
--origincert value ~/.cloudflared/cert.pem TUNNEL_ORIGIN_CERT
Specifies the Tunnel certificate for one of your zones, authorizing the client to serve as an origin for that zone. A certificate is required to use Argo Tunnel. You can obtain a certificate by using the login command or by visiting https://dash.cloudflare.com/argotunnel.
--no-tls-verify
Syntax Default
--no-tls-verify false
Disables TLS verification of the certificate presented by your origin. Will allow any certificate from the origin to be accepted. The connection from your machine to Cloudflare's Edge is still encrypted and verified using TLS.
--metrics
Syntax Default Environment Variable
--metrics value localhost: TUNNEL_METRICS
Address to query for usage metrics.
--metrics-update-freq
Syntax Default Environment Variable
--metrics-update-freq duration 5s TUNNEL_METRICS_UPDATE_FREQ
Frequency to update tunnel metrics.
--tag
Syntax Environment Variable
--tag KEY=VALUE TUNNEL_TAG
Custom tags used to identify this tunnel, in format KEY=VALUE. Multiple tags may be specified by delimiting them with commas e.g. KEY1=VALUE1,KEY2=VALUE2.
--loglevel
Syntax Default Environment Variable
--loglevel value info TUNNEL_LOGLEVEL
Specifies the verbosity of logging. The default info is not noisy, but you may wish to run with warn in production. Available options: panic fatal error warn info debug
--proto-loglevel
Syntax Default Environment Variable
--proto-loglevel warn TUNNEL_PROTO_LOGLEVEL
Specifies the verbosity of the HTTP/2 protocol logging. Any value below warn is noisy and should only be used to debug low-level performance issues and protocol quirks.
--retries
Syntax Default Environment Variable
--retries value 5 TUNNEL_RETRIES
Maximum number of retries for connection/protocol errors. Retries use exponential backoff (retrying at 1, 2, 4, 8, 16 seconds by default) so increasing this value significantly is not recommended.
--pidfile
Syntax Environment Variable
--pidfile value TUNNEL_PIDFILE
Write the application's PID to this file after the first successful connection. Mainly useful for scripting and service integration.
--logfile
Syntax Environment Variable
--logfile value TUNNEL_LOGFILE
Save application log to this file. Mainly useful for reporting issues.
--help
Syntax
--help
Shows help text.
--version
Syntax
--version
Prints the version number and build date.
Login command
cloudflared tunnel login
Opens a special section of the Cloudflare dashboard for obtaining a Tunnel certificate.
It should open your browser automatically and prompt you to log in to your Cloudflare account (unless you previously logged in with 'Remember me' selected). If running cloudflared on a server, you will be given an URL that you can visit on another machine. After logging in, a list of your zones will appear. Select the zone you want to use Argo Tunnel with. After confirming your authorization, the certificate should be sent to the Tunnel client and saved to .cloudflared/cert.pem in your user folder. If this process fails for any reason, the certificate will instead be downloaded by your browser and you will have to copy the file manually to that location. You can also obtain a Tunnel certificate independently of this command by visiting https://dash.cloudflare.com/argotunnel.
Service commands
cloudflared service install
cloudflared service uninstall
Install or uninstall cloudflared as a system service. The details of service installation depend on the OS you are using.
Update command
cloudflared update
Looks for a new version on the official download server. If a new version exists, updates the agent binary and quits. Otherwise, it does nothing. To determine if an update happened in a script, check for error code 64.
Ingress rules
You can configure ingress rules to proxy traffic from multiple hostnames to multiple services using a single instance of cloudflared and a single Argo Tunnel.
Each incoming request received by cloudflared causes cloudflared to send a request to a local service. By configuring ingress rules in the configuration file, you can specify which local services a request should be proxied to.
You can define ingress rules inside of the configuration file.
===== Requirements ===== Configuration files that contain ingress rules must always include a catch-all rule that concludes the ingress file.
In the following example, - service: http_status:404 serves as the catch-all rule for the file.
The file also includes the Tunnel UUID, path to the credentials file, and two ingress rules. The Tunnel UUID or name can alternatively be specified in the tunnel run command and the path to the credentials file can be excluded if it is located at the default filepath.
tunnel: 6ff42ae2-765d-4adf-8112-31c55c1551ef
credentials-file: /root/.cloudflared/6ff42ae2-765d-4adf-8112-31c55c1551ef.json
ingress:
- hostname: gitlab.widgetcorp.tech
service: http://localhost:80
- hostname: gitlab-ssh.widgetcorp.tech
service: ssh://localhost:22
- service: http_status:404
Matching traffic
When cloudflared gets an incoming request, it evaluates each ingress rule from top to bottom to find which rule matches the request. Rules can match either the hostname or path of an incoming request, or both.
If a rule doesn't specify a hostname, all hostnames will be matched. If a rule doesn't specify a path, all paths will be matched.
The last rule you list in the config file must be a catch-all rule that matches all traffic.
This is an example config file that specifies several different rules:
tunnel: 6ff42ae2-765d-4adf-8112-31c55c1551ef
credentials-file: /root/.cloudflared/6ff42ae2-765d-4adf-8112-31c55c1551ef.json
ingress:
# Rules map traffic from a hostname to a local service:
- hostname: example.com
service: https://localhost:8000
# Rules can match the request's path to a regular expression:
- hostname: static.example.com
path: /*.(jpg|png|css|js)
service: https://localhost:8001
# Rules can match the request's hostname to a wildcard character:
- hostname: "*.example.com"
service: https://localhost:8002
# An example of a catch-all rule:
- service: https://localhost:8003
Supported protocols
In addition to HTTP, cloudflared supports protocols like SSH, RDP, arbitrary TCP services, and unix sockets. See a list of supported protocols.
You can also route traffic to the built-in Hello World test server. This is useful when you need to test your Argo Tunnel protocol.
tunnel: 6ff42ae2-765d-4adf-8112-31c55c1551ef
credentials-file: /root/.cloudflared/6ff42ae2-765d-4adf-8112-31c55c1551ef.json
ingress:
# Example of a request over TCP:
- hostname: example.com
service: tcp://localhost:8000
# Example of a request over a Unix socket:
- hostname: staging.example.com
service: unix:/home/production/echo.sock
# Example of a request mapping to the Hello World test server:
- hostname: test.example.com
service: hello_world
# Example of a rule responding to traffic with an HTTP status:
- service: http_status:404
With the catch-all rule, you can set cloudflared to respond to traffic with an HTTP status.
Service Description Example service value HTTP/S Incoming HTTP requests are proxied directly to your local service https://localhost:8000 HTTP/S over unix socket Just like HTTP/S, but using a unix socket instead unix:/home/production/echo.sock TCP, RDP, SSH, SMB, kubectl to a single address TCP requests are proxied to your local service. Learn more. ssh://localhost:2222 TCP, RDP, SSH, SMB, kubectl bastion mode cloudflared will act like a jumphost, allowing access to any local address. bastion Hello World Test server for validating your Argo Tunnel setup Hello_world HTTP status Responds to all requests with the given HTTP status http_status:404
Single-service configuration
If you need to proxy traffic to only one local service, you can do so using the config file. As an alternative, you can set up single-service configurations using command line flags.
This is an example of a single service configured on the command line:
cloudflared tunnel --url localhost:8000 --no-chunked-encoding run mytunnel
Validating your configuration
To validate the ingress rules in your configuration file, run:
$ cloudflared tunnel ingress validate
This will ensure that the set of ingress rules specified in your config file is valid.
Testing your configuration
To verify that cloudflared will proxy the right traffic to the right local service, use cloudflared tunnel ingress rule. This checks a URL against every rule, from first to last, and shows the first rule that matches. For example:
$ cloudflared tunnel ingress rule https://foo.example.com Using rules from /usr/local/etc/cloudflared/config.yml Matched rule #3 hostname: *.example.com service: https://localhost:8000
Origin configurations
You can define the way that cloudflare sends requests to each service by specifying additional configuration options. The following example sets a 30-second connection timeout for all services except for one.
tunnel: 6ff42ae2-765d-4adf-8112-31c55c1551ef
credentials-file: /root/.cloudflared/6ff42ae2-765d-4adf-8112-31c55c1551ef.json
originRequest: # Root-level configuration
connectTimeout: 30s
ingress:
# This service inherits all configuration from the root-level config, i.e.
# it will use a connectTimeout of 30 seconds.
- hostname: example.com
service: localhost:8000
- hostname: example2.com
service: localhost:8001
# This service overrides some root-level config.
- service: localhost:8002
originRequest:
connectTimeout: 10s
disableChunkedEncoding: true
# Some built-in services (like `http_status`) don't use any config. So, this
# rule will inherit all the config, but won't actually use it (because it just
# responds with HTTP 404).
- service: http_status:404
connectTimeout
Default: 30s
Timeout for establishing a new TCP connection to your origin server. This excludes the time taken to establish TLS, which is controlled by [tlsTimeout]({{< ref "#tlsTimeout" >}}).
tlsTimeout
Default: 10s
Timeout for completing a TLS handshake to your origin server, if you have chosen to connect Tunnel to an HTTPS server.
tcpKeepAlive
Default: 30s
The timeout after which a TCP keepalive packet is sent on a connection between Tunnel and the origin server.
noHappyEyeballs
Default: false
Disable the "happy eyeballs" algorithm for IPv4/IPv6 fallback if your local network has misconfigured one of the protocols.
keepAliveConnections
Default: 100
Maximum number of idle keepalive connections between Tunnel and your origin. This does not restrict the total number of concurrent connections.
keepAliveTimeout
Default: 1m30s
Timeout after which an idle keepalive connection can be discarded.
httpHostHeader
Default: ""
Sets the HTTP Host header on requests sent to the local service.
originServerName
Default: ""
Hostname that cloudflared should expect from your origin server certificate.
caPool
Default: ""
Path to the CA for the certificate of your origin. This option should be used only if your certificate is not signed by Cloudflare.
noTLSVerify
Default: false
Disables TLS verification of the certificate presented by your origin. Will allow any certificate from the origin to be accepted.
disableChunkedEncoding
Default: false
Disables chunked transfer encoding. Useful if you are running a WSGI server.
proxyAddress
Default: 127.0.0.1
cloudflared starts a proxy server to translate HTTP traffic into TCP when proxying e.g. SSH or RDP. This configures the listen address for that proxy.
proxyPort
Default: 0
cloudflared starts a proxy server to translate HTTP traffic into TCP when proxying e.g. SSH or RDP. This configures the listen port for that proxy. If set to zero, an unused port will randomly be chosen.
proxyType
Default: ""
cloudflared starts a proxy server to translate HTTP traffic into TCP when proxying e.g. SSH or RDP. This configures what type of proxy will be started. Valid options are
"" for the regular proxy "socks" for a SOCKS5 proxy. See kubectl for more.
zweiter Tunnel auf Linux
nachdem schon ein Tunnel mit zerti als Service läuft, kann ein zweiter auf dem selben Host so erstellt werden:
- sudo cloudflared --hostname neu.domain.ch --hello-world
- müsste nun eine testseite auf https://neu.domain.ch erscheinen
- sudo cp /etc/cloudflared/config.yml /etc/cloudflared/config_neu.yml
- sudo nano /etc/cloudflared/config_neu.yml anpassen auf die neue Seite
- sudo cp /etc/systemd/system/cloudflared.service /etc/systemd/system/cloudflared_neu.service
- sudo nano /etc/systemd/system/cloudflared_neu.service
[Unit] Description=Argo Tunnel neu After=network.target [Service] TimeoutStartSec=0 Type=notify ExecStart=/usr/local/bin/cloudflared --config /etc/cloudflared/config_neu.yml --origincert /etc/cloudflared/cert.pem --autoupdate-freq 24h Restart=on-failure RestartSec=5s [Install] WantedBy=multi-user.target
- sudo systemctl start cloudflared_neu
- Wie den Service zu enablen um automatisch zu starten hab ich noch nicht gefunden - pendent